What is Data at Rest? It’s not as relaxing as it seems.
We live in a hustle-bustle age when everyone seems to be constantly on the move. But all things need to take a break now and then, including the data in your computer systems. When data is currently being stored in a system, that is called Data at Rest. Most systems employ some form of data storage for operation. This could be data on a hard drive, flash drive, SD card, or other devices. To learn more about protecting this resting form of data, let’s return to the network scenario we introduced in our Data in Motion blog.
Security camera network
Our example company has implemented a security camera network to help monitor a restricted portion of their property. There are several cameras with each connected to the network using an ethernet cable. Users can access the video feeds and control the cameras using an on-site computer. All the camera footage is also stored in a database on an off-site server, and users can view the logged footage remotely using an authorized computer on the network.
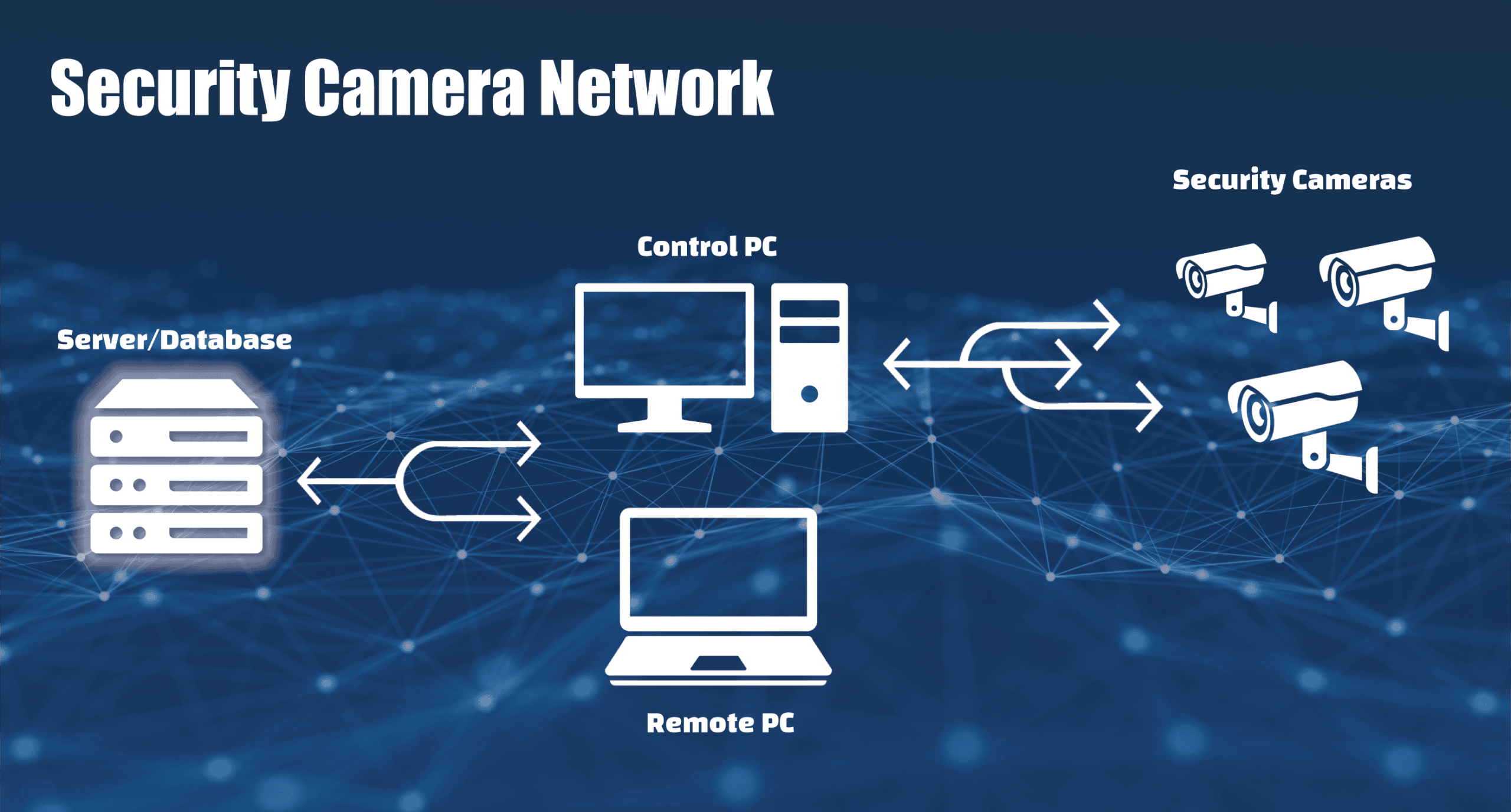
This system uses all the data targets that we covered in our Introduction to Secure Data. Today, let’s focus on Data at Rest. Where Data in Motion is vulnerable because it’s moving between systems, Data at Rest is vulnerable because it’s persistent. All an attacker has to do is obtain or copy the drive/media storing the data and they will have “indefinite” access to that data. Depending on how it is obtained, the owner may have no idea they’ve been compromised or could lose access to their important data. Neither case is ideal!
Why is Data at Rest vulnerable? Because attackers have all the time they need.
Vulnerabilities:
- By nature, Data at Rest is persistent and copies can be made.
- Can contain useful or valuable information about a person, company, system, etc.
- Storage media/devices can be physically removed from a system.
Goals of attackers:
- Run algorithms to obtain credentials or encryption keys.
- Collect data in pieces to assemble a bigger picture.
- Deny or prevent access to stored data.
- Collect data for malicious use.
How do I protect Data at Rest? Changing your defense based on the offense.
In our security camera scenario, Data at Rest are the video files being stored in the database and the configuration information stored on the network systems. There are several ways hackers can attempt to compromise the data.
Scraping: collecting data for later use.
This is Data at Rest’s equivalent of Data in Motion’s sniffing. Scraping collects Data at Rest for later use, often without permission of the owner. Scraping information allows an attacker to assemble many small pieces into a bigger picture. In our example, an attacker who is scraping the database could determine the security camera coverage patterns over time. This could help them identify blind spots in the system and allow them to devise a pathway to enter the company’s secure property undetected. Scraping attacks should be protected against through user-authentication and encryption of data.
Brute force attack: the tortoise to your hare.
Even though your Data at Rest is encrypted or locked behind user authentication, it is still technically vulnerable. A brute force attack may not be the fastest attack, but it will eventually work given enough time. This will allow an attacker to crack your credentials or keys, allowing access to otherwise secure data. In our example, an attacker could gain unauthorized access to the database through brute force login attempts. They might also try to copy data and use it to obtain the system’s encryption keys, effectively bypassing the protections. The best way to guard against a brute force attack is using dynamic protection schemes that regularly change encryption keys and/or credentials. Rotating the keys and credentials forces an attacker to complete their attack within a limited time and minimizes potential damage. When the credentials change, the attacker would have to start over — severely limiting their chances of success.
Physical attacks: hope you made a backup.
A physical attack could be removing or destroying a drive or media containing Data at Rest. At best, the attacker might simply want to prevent access to the data. At worst, the attacker might be able to insert the drive into another system to gain access. In our example, what if an attacker was able to obtain the drives from the server? They may want to prevent the company from seeing something incriminating on the recorded video feed. It also gives them time to perform a brute force attack that could further compromise the network security. Site security, tamper evidence and response, and user authentication can all be used to protect your Data at Rest to ensure the integrity of the system.
Do your best.
Some inspirational quotes say, “Do your best and forget the rest.” But as we’ve discovered, Data at Rest introduces several vulnerabilities to your computer networks and creates the need for special protections. Watch for our next article, where we go into more detail about Data in Use and how to protect your systems using Crystal Group hardware and components.